Hello Cybersecuriters! 🍩
Before you scroll down and enjoy this week's newsletter, why not join our LinkedIn Group to keep in touch and see our updates. Click here to join.
This is what you missed this week, and read the newsletter for more
💻 Google Uncovers 18 Severe Security Vulnerabilities in Samsung Exynos Chips
💻 Critical Vulnerability Discovered in WooCommerce Payments
📈 LockBit brags To Leak Thousands of SpaceX Blueprints Stolen From Supplier
📈 Operation Soft Cell: Chinese Hackers Breach Middle East Telecom Providers
🚨 Chinese-linked hackers deployed the most zero-day vulnerabilities in 2022
🚨 Twitter testing government ID-based verification, new screenshots show
⚖️ Big Tech companies are pushing for changes to a spy law
Enjoy this weekly newsletter.
💻 Malware and Vulnerabilities
Google Uncovers 18 Severe Security Vulnerabilities in Samsung Exynos Chips
Google's Project Zero has identified multiple vulnerabilities that could allow attackers to remotely execute code on mobile devices. The vulnerabilities affect various chipsets, including Qualcomm, MediaTek, and Samsung Exynos, and could be exploited via the internet, SMS, or other methods.
The vulnerabilities could enable attackers to take complete control of the affected devices, including accessing data, making calls and sending messages, and installing malware. The affected devices include popular models from Samsung, Xiaomi, and Google's own Pixel line. The discovery highlights the importance of regular software updates and the need for manufacturers to prioritize security in their products. However, four vulnerabilities are being withheld from disclosure. [read more]

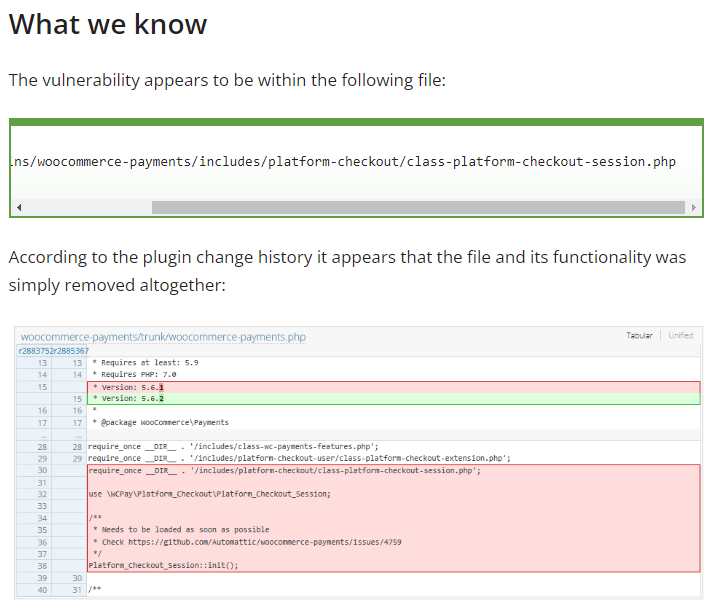
Critical Vulnerability Discovered in WooCommerce Payments
Sucuri, a cybersecurity firm, has recently discovered a critical vulnerability in WooCommerce Payments, a popular payment platform used by many e-commerce websites. The vulnerability could allow attackers to bypass the platform's security measures and gain access to sensitive customer data, such as payment card information.
The vulnerability was found in the plugin's code, which handles the encryption and decryption of customer data. If exploited, attackers could potentially intercept and steal customer data during the payment process, which could lead to financial losses and damage to the affected websites' reputation. [read more]
📈 Breaches and Incidents
LockBit brags To Leak Thousands of SpaceX Blueprints Stolen From Supplier
A ransomware gang called LockBit has claimed responsibility for a recent attack on SpaceX's internal systems. The gang has demanded $50 million in ransom, threatening to release sensitive data if the demand is not met. SpaceX has confirmed the attack and stated that it has taken steps to mitigate the impact.
LockBit is known for targeting large organizations and demanding high ransoms; its tactics include exploiting vulnerabilities in systems and using social engineering techniques to gain access to networks. The incident highlights the continued threat of ransomware attacks and the need for robust cybersecurity measures to protect against them. [read more]
Attackers hit Bitcoin ATMs to steal $1.5 million in crypto cash
An attacker was able to gain access to General Bytes' internal systems and install malware that affected the firmware of its crypto ATMs. This allowed the attacker to remotely control the machines and steal cryptocurrency from unsuspecting users.
The attacker reportedly used a phishing email to gain access to General Bytes' network and then used that access to plant the malware on the ATMs. The company has since taken steps to mitigate the attack and is working with law enforcement to investigate the incident. [read more]
Operation Soft Cell: Chinese Hackers Breach Middle East Telecom Providers
A Chinese hacking group known as "Operation Soft Cell" has been conducting espionage against telecommunication companies worldwide, stealing sensitive data from high-profile individuals. The group has been linked to the Chinese government and is believed to be using advanced techniques to remain undetected. The article calls for increased international cooperation and stronger security measures to combat cyber threats like this one. [read more]
🚨 Threat Intel & Info Sharing
Chinese-linked hackers deployed the most zero-day vulnerabilities in 2022
Mandiant researchers have reported a decline in the use of zero-day vulnerabilities, with 55 being observed in 2022, compared to 81 in 2021.
Cybersecurity firm Mandiant has identified two zero-day vulnerabilities that have been used by a group called UNC215. The group is believed to be linked to the Chinese government and is known for attacking organizations in the US, Europe, and Japan. The vulnerabilities could allow the attackers to remotely execute code on targeted systems and gain access to sensitive data.
Mandiant has shared the details of the vulnerabilities with Microsoft and other relevant parties to help mitigate the risk. The discovery highlights the ongoing threat of state-sponsored cyberattacks and the importance of robust cybersecurity measures. [read more]
Twitter testing government ID-based verification, new screenshots show
Twitter is reportedly testing a new verification process based on government-issued IDs. The new process is designed to verify user identities and prevent bots, trolls, and fake accounts from spreading misinformation and engaging in malicious activities on the platform.
The article explains that the new verification process will require users to provide a valid government-issued ID, such as a driver's license or passport, to prove their identity. Once verified, users will receive a blue checkmark badge next to their usernames, indicating that their accounts are authentic and trustworthy.
While this new verification process could potentially improve the overall user experience on Twitter by reducing the presence of fake accounts and bots, it also raises some concerns about privacy and security. Users who provide their personal information to Twitter may become vulnerable to identity theft and other cyber threats if their data is mishandled or stolen.
It's worth noting that Twitter has been under fire in recent years for its handling of user data and security breaches. In 2020, the platform suffered a massive security breach that resulted in several high-profile accounts, including those of Elon Musk and Barack Obama, being hacked by an attacker who gained access to Twitter's internal systems. [read here]
📊 Trends, Reports, Analysis
ENISA Transport Threat Landscape
The European Union Agency for Cybersecurity (ENISA) has recently published a report discussing the various cyber threats faced by the transportation industry. The article highlights the growing dependence of the transportation sector on information technology and the internet, which makes it more vulnerable to cyber attacks.
The report outlines several types of cyber threats that could affect the transportation industry, such as ransomware attacks, phishing scams, and supply chain attacks. It also discusses the potential consequences of a successful attack, which could include operational disruptions, financial losses, and damage to the industry's reputation. [read the report here]

⚖️ Laws, Policy, Regulations
The Spy Law That Big Tech Wants to Limit
Big Tech companies are pushing for changes to a spy law that allows the government to access user data without a warrant, arguing for more transparency and limitations on government surveillance.
The debate over the spy law highlights the ongoing tension between privacy concerns and national security interests.
Tech companies and their lobbying organizations want the ability to publicly disclose more information about how many times the government requests information about their users and customers and what kind of data they are being forced to hand over. [read more]
🎙 Podcast Recommendations
The best way to break in is to walk through the front door.
Joe describes one of history's great con artists, Victor Lustig, who sold the Eiffel Tower. Twice. Dave shares a story from a listener involving a UPS tracking number scam. The catch of the day involves an attempted romance scam on the XBOX platform. Dave interviews Sherri Davidoff, CEO of LMG Security and is the hacker named "Alien" in Jeremy Smith's book, "Breaking and Entering." She has her own book, "Data Breaches: Crisis and Opportunity." [listen here]
😊 Picture of the week

We hope you enjoyed your weekly digest! ☕🥮
If you liked our content, be a part of our Cybersecurity journey, then you can join our communities below or go to The Cybersecurity Club for resources.
Signing off! Stay safe and we’ll see you soon.
