Hello Cybersecuriters! 🍩
This is what you missed this week
Yandex Code Repositories Leaked Allegedly by Former Employee
GoTo Says Hackers Stole Encrypted Backups, MFA Settings
FBI shuts down Hive ransomware gang that targeted schools and hospitals
Global Cybersecurity Outlook 2023 From World Economic Forum Annual Meeting
ENISA gives out 'do it yourself' toolbox for creating security awareness programs
Enjoy this weekly newsletter.
💻 Malware and Vulnerabilities
Lexmark releases security firmware update for remote code execution flaw impacting over 100 printer models (CVE-2023-23560)
The vulnerability is a server-side request forgery (SSRF) in the Web Services feature of Lexmark printers, it received a CVSS score 9.0.
The compromise of a vulnerable printer can be exploited by threat actors to achieve an initial foothold in the target network.
The company is not aware of any attacks in the wild exploiting the vulnerability.[read more]
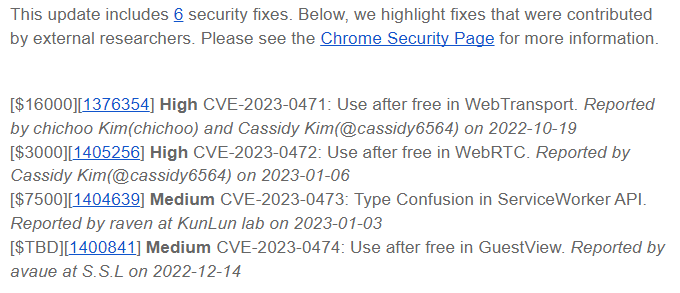
Google Chrome 109 update addresses six security vulnerabilities
Google released Chrome version 109.0.5414.119 for Mac and Linux and 109.0.5414.119/.120 for Windows to fix six vulnerabilities
Four of the vulnerabilities were reported by external researchers who were awarded over $26,500 for their findings
Google is not aware of any attacks in the wild exploiting these vulnerabilities
📈 Breaches and Incidents
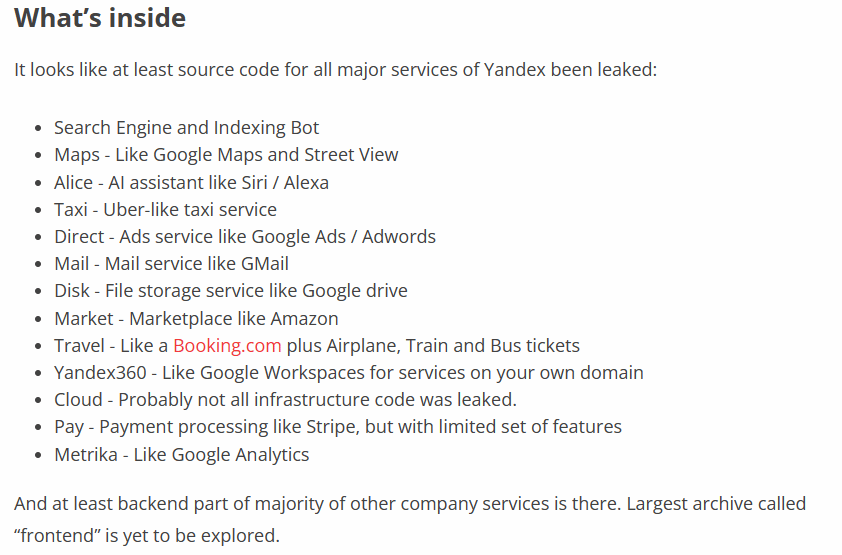
Yandex Code Repositories Leaked Allegedly by Former Employee
The source code of the popular Russian technology company, Yandex, has been leaked on a hacker forum. The leak includes backend services such as the Yandex search engine, Yandex Maps, AI assistant "Alice," Yandex Taxi, Yandex Travel, Ads service "Yandex Direct" and analytics service Metrika, Yandex 360, Yandex Market, Yandex Pay and Yandex Cloud. The data was stolen by a former employee and leaked in July 2022.
Although the leak does not include any customer data and the exposed code may not be 100% identical to the code currently used by Yandex, the leak does present a chance for hackers to find security flaws and craft specialized exploits. Former Yandex employee, Grigory Bakunov, has warned that the leaked code might be up to 90% similar to the code currently used in the company's operational services, making it possible for threat actors to discover potential vulnerabilities in Yandex's systems.
GoTo Says Hackers Stole Encrypted Backups, MFA Settings
IT management software firm GoTo was affected by a security breach in 2022 where an unknown threat actor stole encrypted backups and an encryption key for a portion of that data.
The affected data included account usernames, salted and hashed passwords, a portion of Multi-Factor Authentication (MFA) settings, as well as some product settings and licensing information. The company plans to reset the passwords of affected users and/or reauthorize MFA settings where applicable, and migrating their accounts onto an enhanced Identity Management Platform for additional security.
🚨 Threat Intel & Info Sharing
FBI shuts down ransomware gang that targeted schools and hospitals
The FBI has seized the computer infrastructure used by a notorious ransomware gang, known as Hive, which has extorted more than $100 million from victims around the world.
The FBI and other law enforcement agencies have been actively tracking the group for several months and announced that they have seized the group's computer infrastructure in a coordinated action. The FBI Director, Christopher Wray, stated that they had extraordinary access to the group's computer networks, allowing them to pass decryption keys to victims and prevent $130 million in ransom payments.
The Hive ransomware group is a notorious cybercriminal group that has been active for several years. They are known for using ransomware attacks to extort large sums of money from victims around the world, targeting a wide range of organizations including hospitals, schools, and businesses. The group has been responsible for extorting over $100 million from victims, according to US officials. [read more]

Australia fronts International Counter Ransomware Taskforce
37 participating member countries established the Counter Ransomware Initiative (CRI) to hold ransomware actors accountable for their crimes, combat their ability to profit from illicit proceeds and disrupt and bring them to justice.
The CRI established a task force to develop cross-sectoral tools, exchange cyber threat intelligence, and increase early warning capabilities and prevent attacks. The task force would also help consolidate policy and best practice frameworks. The task force was established in the Australian Department of Home Affairs’ Cyber and Critical Technology Coordination Centre.[read more]
📊 Trends, Reports, Analysis
Global Cybersecurity Outlook 2023 From World Economic Forum Annual Meeting
The Global Cybersecurity Outlook 2023 examines the cybersecurity trends that will impact our economies and societies in 2023. The report includes the results of new research on how leaders are responding to cyber threats now and provides recommendations on what leaders can do to secure their organisations in the year to come.
“The most striking finding that we’ve found,” WEF managing director Jeremy Jurgens said during a presentation highlighting the WEF Global Security Outlook Report 2023, “is that 93 percent of cyber leaders, and 86 percent of cyber business leaders, believe that the geopolitical instability makes a catastrophic cyber event likely in the next two years. This far exceeds anything that we’ve seen in previous surveys.”[watch here]
⚖️ Laws, Policy, Regulations
Cybersecurity Awareness Raising: Peek Into the ENISA-Do-It-Yourself Toolbox
The European Union Agency for Cybersecurity (ENISA) launches today the “Awareness Raising in a Box (AR-in-a-BOX)” package designed to help organisations build their own awareness raising programmes.
Awareness raising programmes form an indispensable part of an organisation’s cybersecurity strategy and are used to promote good practices and induce change in the cybersecurity culture of employees and ultimately the society at large.[read more]
🎙 Podcast Recommendations
ChatGPT is a bigger threat to cybersecurity than most realize
A language-generating AI model called ChatGPT, available for free, has taken the internet by storm. While AI has the potential to help IT and security teams become more efficient, it also enables threat actors to develop malware.
In this interview with Help Net Security, Daniel Spicer, Chief Security Officer for Ivanti, talks about what this technology means for cybersecurity.[read the interview]
🎙 Picture of the week

We hope you enjoyed your weekly digest! ☕🥮
If you liked our content, be a part of our Cybersecurity journey, then you can join our communities below or go to The Cybersecurity Club for resources.
Signing off! Stay safe and we’ll see you soon.
