Hello Cybersecuriters! 🍩
This is what you missed this week
City of London on High Alert After Ransomware Attack on Financial Data Group
Lockbit ransomware operators have released a new version of their malware, LockBit Green, that also targets cloud-based services.
Hacker groups are offering six-figure salaries, bonuses, and paid leaves to attract talent on dark web
New “MITRE ATT&CK-like” framework outlines software supply chain attack TTPs
Enjoy this weekly newsletter.
💻 Malware and Vulnerabilities
City of London on High Alert After Ransomware Attack
Ion Cleared Derivatives, a key supplier of trading software for derivatives trading worldwide, suffered a "cybersecurity event" that affected some of its services and reportedly impacted 42 clients.
The Futures Industry Association (FIA) confirmed the network issues caused by the cyber-incident at Ion have impacted the trading and clearing of exchange-traded derivatives worldwide and is coordinating communication and information sharing with relevant parties to assess the extent of the impact and mitigate the disruption. The attack has raised concerns about the interdependencies of the financial system and the potential knock-on impact on confidence in the financial system.[read more]
Lockbit ransomware operators have released a new version of their malware, LockBit Green, that also targets cloud-based services.
Lockbit ransomware operators have implemented a new version of their malware, dubbed LockBit Green, which was designed to include cloud-based services among its targets.
This is the third version of the ransomware developed by the notorious gang, after the Lockbit Red and Lockbit Black ones. Affiliates to the Lockbit RaaS can obtain LockBit Green using the builder feature on the LockBit portal.[read tweet]
📈 Breaches and Incidents
Google Fi says hackers accessed customers’ information
Google’s cell network provider Google Fi has confirmed a data breach, likely related to the recent security incident at T-Mobile, which allowed hackers to steal millions of customers’ information.
In an email sent to customers on Monday, obtained by TechCrunch, Google said that the primary network provider for Google Fi recently informed the company that there had been suspicious activity relating to a third-party support system containing a “limited amount” of Google Fi customer data.
The timing of the notice — and the fact that Google Fi uses a combination of T-Mobile and U.S. Cellular for network connectivity — suggests the breach is linked tothe most recent T-Mobile hack. [read more]
BlackCat Ransomware Hits Defence Contractor, Steals Weapons Data
The BlackCat (ALPHV) ransomware group claims to have hacked the industrial explosives manufacturer Solar Industries India Limited. It has stolen over 2 TB of critical data, including designs of weapons currently in use.[read more]

🚨 Threat Intel & Info Sharing
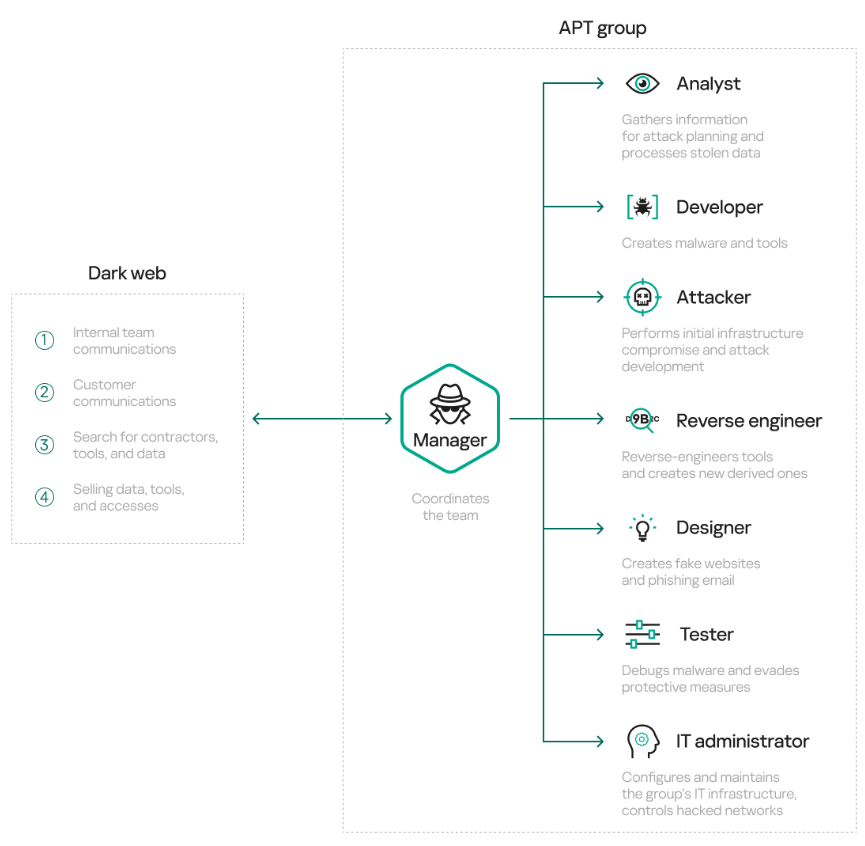
Cybercrime groups offer six-figure salaries, bonuses, paid time off to attract talent on dark web
Cybercrime is a growing market and cybercriminals are offering high salaries and perks to attract skilled workers such as developers, administrators, and designers.
A recent analysis by cybersecurity firm Kaspersky found that job posts related to cybercrime on dark web forums have exceeded 10,000 per quarter, with developers being the most sought after. Despite the high salaries offered, researchers warn that the reasons for seeking employment in this field may not be fully understood and that the salaries are often not significantly higher than what can be earned legally. [read more]
New “MITRE ATT&CK-like” framework outlines software supply chain attack TTPs
A new open framework has been launched to outline a comprehensive and actionable way for businesses and security teams to understand attacker behaviors and techniques specifically impacting the software supply chain.
The Open Software Supply Chain Attack Reference (OSC&R) initiative, led by OX Security, evaluates software supply chain security threats, covering a wide range of attack vectors including vulnerabilities in third-party libraries and components, supply chain attacks on build and deployment systems, and compromised or malicious software updates. [read more]
Dutch, European Hospitals ‘Hit by Pro-Russian Hackers’
Dutch cyber authorities said Wednesday that several hospital websites in the Netherlands and Europe were likely targeted by a pro-Kremlin hacking group because of their countries’ support for Ukraine.
The UMCG hospital in the northern Dutch city of Groningen, one of the largest in the country, saw its website crash in a cyberattack on Saturday.“European hospitals including in the Netherlands have most likely been hit by the pro-Russian hacking group Killnet,” said the Dutch National Cyber Security Centre (NCSC)[read more]
📊 Trends, Reports, Analysis
50% of organizations have indirect relationships with 200+ breached fourth-party vendors
98 percent of organizations have vendor relationships with at least one third-party that has experienced a breach in the last two years, according to SecurityScorecard and The Cyentia Institute
The study also found that 50 percent of organizations have indirect relationships with at least 200 breached fourth-party vendors in the last two years.
While examining the regional dimension of third-party relationships, SecurityScorecard found that 59% of organizations have vendors from five or fewer countries, while roughly 14% work with vendors spanning 10 or more countries
⚖️ Laws, Policy, Regulations
Cybersecurity Awareness Raising: Peek Into the ENISA-Do-It-Yourself Toolbox
President Biden is about to approve a policy that goes much farther than any previous effort to protect private companies from malicious hackers—and to retaliate against those hackers with our own cyberattacks.
The 35-page document, titled “National Cybersecurity Strategy,” differs from the dozen or so similar papers signed by presidents over the past quarter-century in two significant ways: First, it imposes mandatory regulations on a wide swath of American industries. Second, it authorizes U.S. defense, intelligence, and law enforcement agencies to go on the offensive, hacking into the computer networks of criminals and foreign governments, in retaliation to—or preempting—their attacks on American networks. [read more]
🎙 Podcast Recommendations
Darknet Diaries: EP 130: JASON'S PEN TEST
Jason Haddix is a renowned penetration tester who has made a name for himself by uncovering vulnerabilities in some of the world’s biggest companies. In this episode, Jason shares his funny and enlightening stories about breaking into buildings and computers and talks about the time he discovered a major security flaw in a popular mobile banking app. [listen here]
🎙 Picture of the week

We hope you enjoyed your weekly digest! ☕🥮
If you liked our content, be a part of our Cybersecurity journey, then you can join our communities below or go to The Cybersecurity Club for resources.
Signing off! Stay safe and we’ll see you soon.
