Hello Cybersecuriters! 🍩
This is what you missed this week
💻 GitHub's New Feature Is A Game-Changer For Preventing Security Breaches In Your Code Repositories
💻BlackLotus UEFI Bootkit Discovered - Is Your Computer Vulnerable to Undetectable Malware Attacks
🚨 Bidencash 2 million credit cards leaked in massive breach
🚨 CISA Reveals Secret Red-Team Exercise on Major Critical Infrastructure Network
🚨 Russia Bans Top Messaging Apps from WhatsApp, Discord, Microsoft Teams, Telegram and more..
⚖️ New National Cybersecurity Strategy Unveiled by Biden-Harris Administration
Enjoy this weekly newsletter.
💻 Malware and Vulnerabilities
GitHub's New Feature Is A Game-Changer For Preventing Security Breaches In Your Code Repositories
GitHub has introduced a new feature called "Secret Scanning Alerts" that helps developers detect and address sensitive information, such as passwords or API keys, that may have been inadvertently exposed in their public code repositories. This feature was previously only available to users of GitHub's paid plans, but is now accessible to all users of public repositories.
This new feature is important because it helps prevent security breaches that could occur if sensitive information is left exposed in code repositories. By making this feature available to all public repositories, GitHub is helping to raise awareness of the importance of protecting sensitive information and making it easier for developers to maintain the security of their code. [read more]
First-Ever UEFI Bootkit Discovered - Is Your Computer Vulnerable to Undetectable Malware Attacks?
The cybersecurity firm BlackLotus has developed a new type of malware called a UEFI bootkit, which is designed to infect computer systems at a very low level and remain undetected by traditional antivirus software. This type of malware is particularly dangerous because it can bypass many of the security measures that are built into modern operating systems.
The impact of this development is potentially significant for everyone who uses a computer, as it could make it easier for cybercriminals to gain access to sensitive data, steal identities, or launch other types of attacks.
The next steps for computer users are to stay vigilant and ensure that they have up-to-date antivirus software installed on their systems. It is also important to avoid clicking on suspicious links or downloading unknown files, and to be cautious about entering personal information online. Cybersecurity experts will continue to monitor the development of UEFI bootkits and other types of malware to identify new threats and develop effective countermeasures. [read tweet]

📈 Breaches and Incidents
Chick-fil-A customers beware! Hackers steal your personal info in massive months-long attack - are YOU a victim?
CChik-fil-A confirmed that its customers' accounts were hacked in an automated attack that lasted several month. The attack occurred over a period of several months but the exact timeline has not been disclosed.
Hackers used a technique called credential stuffing, which involves using stolen usernames and passwords from other sites to gain unauthorized access to accounts on Chick-fil-A's website.
It is not yet clear how many customers were affected, but Chick-fil-A has said that they will be contacting those whose accounts were compromised and will be providing them with free credit monitoring services. [read more]

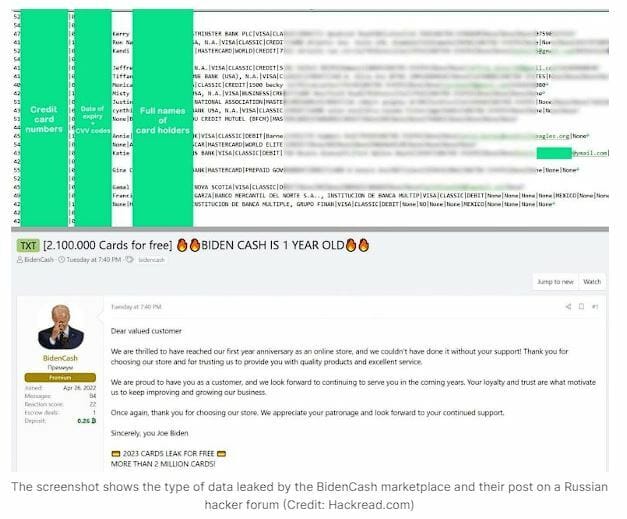
Bidencash 2 million credit cards leaked in massive breach
The personal information of 2 million credit card users was leaked through a breach of a third-party payment processor called Bidencash. The breach was caused by a misconfigured Elasticsearch database that allowed unauthorized access to the sensitive data. The leaked information included names, addresses, phone numbers, email addresses, and credit card details.
Hackers have been selling the stolen credit card information on the dark web, and researchers have identified a vendor selling the data under the name "SkuVault." The vendor is selling the credit card data for around $10 per card. [read more]
🚨 Threat Intel & Info Sharing
CISA Reveals Secret Red-Team Exercise on Major Critical Infrastructure Network
The Cybersecurity and Infrastructure Security Agency (CISA) has released a set of key findings from its recent Red Team engagements with government and private sector organizations. The findings are intended to help organizations improve their network monitoring and hardening capabilities by identifying common vulnerabilities and attack methods used by threat actors.
The key findings include the need for better network segmentation, improved access control mechanisms, and increased visibility into network activity. The report also highlights the importance of regular security assessments and vulnerability scanning, as well as the need for effective incident response plans and employee training programs.
Russia's secret cyberattacks revealed - Dutch intelligence warns of shocking number of unreported incidents
The Dutch General Intelligence and Security Service (AIVD) has warned that Russia has carried out a large number of cyberattacks that have not yet been made public. The agency has said that these attacks are part of a broader pattern of aggressive behavior by Russia, including interference in elections and the use of chemical weapons on foreign soil. [read more]
Russian hackers strike again - Poland's tax service website hacked in shocking cyberattack
Poland's Ministry of Finance has attributed a recent cyberattack on its tax service website to Russian hackers. The attack, which occurred on February 28th, temporarily disrupted access to the site and prevented users from filing their tax returns. The ministry has stated that it has taken steps to address the issue and to improve the security of its website. [read more]
Russia Bans Top Messaging Apps in Major Crackdown
On March 1, 2023, restrictions on the use of certain foreign messengers by Russian organizations will come into effect according to the "On Information, Information Technologies and Information Protection" law. The banned messengers include popular services such as Discord, Microsoft Teams, Skype for Business, Snapchat, Telegram, Threema, Viber, WhatsApp, and WeChat. [read more]
📊 Trends, Reports, Analysis
The top 5 states for mobile malware attacks revealed - are you at risk? Kaspersky's 2022 Mobile Threat Report
Kaspersky, a cybersecurity firm, has released its Mobile Threat Report for 2022, which analyzes the mobile threat landscape and provides insights into the types of threats that users face on their mobile devices.
According to the report, the top five states with the highest number of mobile malware attacks are Nigeria, Russia, Iran, Algeria, and Indonesia. The report also highlights the growing threat of banking Trojans, which are designed to steal users' financial information and credentials. Additionally, the report notes that attackers are increasingly using social engineering tactics, such as phishing and smishing, to trick users into downloading malware onto their devices.
The report underscores the importance of staying vigilant and taking steps to protect mobile devices from threats, such as installing security software and avoiding suspicious links and downloads. [read more]

⚖️ Laws, Policy, Regulations
New National Cybersecurity Strategy Unveiled by Biden-Harris Administration
The Biden-Harris administration has released a new National Cybersecurity Strategy aimed at enhancing the security of critical infrastructure, improving incident response capabilities, and promoting international cooperation on cybersecurity issues. The strategy identifies four key pillars:
Defending the homeland by securing federal networks, critical infrastructure, and the public against cyber threats.
Building a more secure and resilient digital ecosystem by improving cybersecurity practices across all sectors and promoting the adoption of secure technologies.
Countering malicious cyber activities by holding malicious actors accountable and working with international partners to establish norms of responsible behavior in cyberspace.
Strengthening cyber incident response and recovery by developing coordinated approaches to incident response and supporting the development of a skilled cybersecurity workforce.
The administration has also announced several initiatives to support the implementation of the strategy, including the creation of a Cyber Safety Review Board and the establishment of a Cybersecurity Talent Initiative to attract and retain cybersecurity talent in the federal government. The strategy represents a comprehensive effort to address the growing threat of cyber attacks and to promote a safer and more secure digital environment. [read more]
🎙 Podcast Recommendations
SECURITY NOW EPISODE 912 THE NSA @ HOME
Hosted by Steve Gibson, Leo Laporte: LastPass hack details, Signal says no to UK, more PyPI troubles, QNAP bug bounty [listen here]
😊 Picture of the week

We hope you enjoyed your weekly digest! ☕🥮
If you liked our content, be a part of our Cybersecurity journey, then you can join our communities below or go to The Cybersecurity Club for resources.
Signing off! Stay safe and we’ll see you soon.
