Hello Cybersecuriters! 🍩
This is what you missed this week
💻 LastPass Hack Highlights Unpatched Software Risks: DevOps Engineer and Customer Data Compromised
💻 Malware-Distributing Phishing Attacks Exploit Microsoft OneNote Files
🚨 Ransomware Gang "The Dark Overlord" Threatens Privacy of Minneapolis Schools - Posts Video of Stolen Personal Data
🚨 FBI Just Admitted It Bought US Location Data
🚨 China employs AI newscasters for state-sponsored propaganda campaign
🚨 Chat GPT got its first Bug Bounty
Enjoy this weekly newsletter.
💻 Malware and Vulnerabilities
LastPass Hack Exposes Dangers of Unpatched Software: Exploiting Plex Flaw Leads to DevOps Engineer Compromise and Customer Data Breach
The article from The Hacker News details the LastPass hack, which was the result of a coordinated attack leveraging stolen information from an earlier incident and a third-party data breach, along with exploiting a vulnerability in a third-party media software package (Plex) to gain access to the home computer of a DevOps engineer. Attackers then used a keylogger malware to obtain the engineer's credentials and breach LastPass's cloud storage environment, ultimately resulting in the theft of partially encrypted password vault data and customer information. [read more]
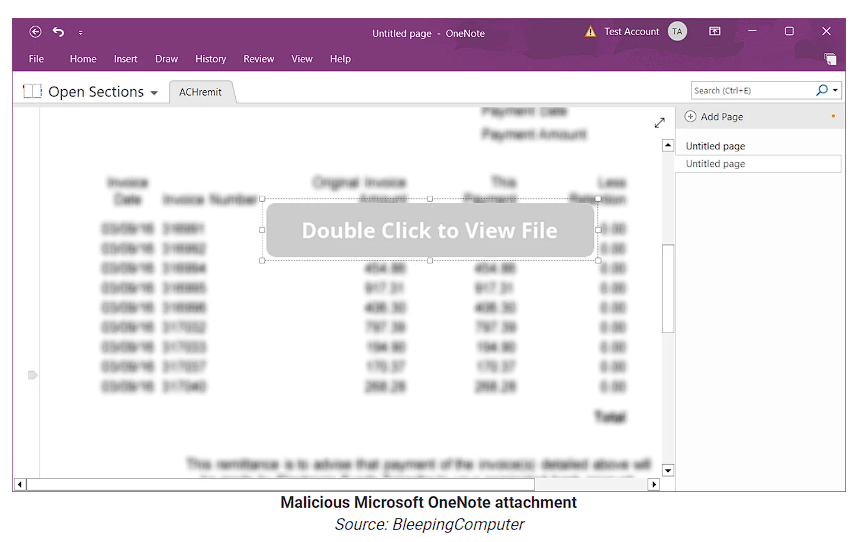
Malware-Distributing Phishing Attacks Exploit Microsoft OneNote Files
Hackers are using Microsoft OneNote files to spread malware and breach corporate networks. Threat actors have been abusing macros in Microsoft Word and Excel documents for years to download and install malware on Windows devices. After Microsoft disabled macros by default in Office documents, threat actors began using other less commonly used file formats to distribute malware.
In mid-December, threat actors began using Microsoft OneNote attachments to distribute malware as they do not distribute malware through macros or vulnerabilities. Instead, threat actors create intricate templates that appear to be a protected document with a message to 'double-click' a design element to view the file, but the 'Double Click to View File' is actually hiding a series of embedded files that sit underneath the button layer.
To prevent malicious Microsoft OneNote attachments from infecting Windows, the best way is to block the '.one' file extension at secure mail gateways or mail servers. If not possible, use Microsoft Office group policies to restrict the launching of embedded file attachments in Microsoft OneNote files. [read more]
📈 Breaches and Incidents
Conservative News Corp. empire says hackers were inside its network for 2 years
News Corp, a global media conglomerate owned by conservative billionaire Rupert Murdoch, reported that hackers were inside its network for two years.
The company's investigation found that the hackers gained access to employee email accounts and stole personal and sensitive information, including financial and business data.
The incident raises concerns about the vulnerability of high-profile media companies to cyberattacks and the potential impact on their operations and the privacy of their employees and customers. [read more]
Ransomware Gang "The Dark Overlord" Threatens Privacy of Minneapolis Schools - Posts Video of Stolen Personal Data
A ransomware gang named "The Dark Overlord" has posted a video on Twitter showing some of the data they claim to have stolen from the Minneapolis Public Schools (MPS) district. The video included personal information such as Social Security numbers, home addresses, and phone numbers belonging to students, parents, and staff members. The district had previously reported a cyberattack in February that disrupted its communication and email systems. MPS officials have stated that they have not paid any ransom demands and are working with law enforcement to investigate the incident. [read more]

Acer server breached, 160GB of confidential information allegedly stolen and put up for sale
Acer has suffered a security breach in which an unidentified attacker claims to have stolen confidential information from one of its document servers for repair technicians. The cyber criminal posted on BreachForums that they were selling a 160GB database that included confidential presentations, technical manuals, and product documents.
Acer has confirmed the incident and stated that there is no indication that any consumer data was stored on the server. However, even if no customer data was stolen, the data dump could still damage Acer as the proprietary and technical information could be valuable to competitors and criminals. [read more]
🚨 Threat Intel & Info Sharing
FBI Just Admitted It Bought US Location Data
The FBI has been purchasing location data from private companies and using it for investigative purposes, without obtaining warrants or other legal process.
This practice has raised concerns about privacy violations and has led to calls for stricter regulation and oversight of the collection and use of location data. [read more]
China employs AI newscasters for state-sponsored propaganda campaign
AI newscasters are being used by China to propagate pro-China propaganda, marking one of the initial cases of state-sponsored propaganda channels employing AI.
Chinese disinformation campaigns have been observed using fake news programs featuring fake people to influence the US public opinion and push propaganda. These programs are designed to look legitimate and credible to unsuspecting viewers.
It's essential to be aware of disinformation tactics and to verify the sources of information we consume. To counter disinformation campaigns, it's important to promote media literacy, fact-checking, and critical thinking skills. Additionally, governments and social media platforms must take responsibility and implement measures to curb disinformation campaigns. [watch here]
Chat GPT got its first Bug Bounty
A user who goes by the name CodeBlue29 was able to leverage ChatGPT to develop a malware that circumvented an EDR solution, despite having no prior experience in creating such malicious software. The purpose of the exercise was to assess the effectiveness of various EDR solutions, and ChatGPT's output proved to be highly capable, successfully bypassing a well-known solution. Furthermore, the malware was submitted as part of a bug bounty program and CodeBlue29 received a payout of $650. [read more]
📊 Trends, Reports, Analysis
CrowdStrike Report Highlights Ransomware, Nation-State Threats, and COVID-19 Phishing Campaigns as Top Cybersecurity Risks in 2023
Ransomware attacks continue to be a significant threat, with criminal groups employing increasingly sophisticated tactics such as double extortion and supply chain attacks.
Nation-state adversaries continue to pose a serious threat, with China, Russia, North Korea, and Iran being the most active and advanced threat actors. These groups target various sectors, including government, defense, critical infrastructure, and technology.
COVID-19-related themes have been widely used in phishing campaigns, with malicious actors exploiting the pandemic to distribute malware, steal credentials, and launch ransomware attacks.
The use of zero-day vulnerabilities, or previously unknown software flaws, remains a popular tactic for advanced threat actors. These vulnerabilities are often sold on underground markets or used in targeted attacks to gain access to high-value targets.
The rise of remote work has created new security challenges, with organizations struggling to secure endpoints, networks, and cloud environments against various threats.
The adoption of new technologies such as 5G, IoT, and AI is creating new attack surfaces, and organizations must implement robust security measures to mitigate the risks. [read the report here]
⚖️ Laws, Policy, Regulations
New National Cybersecurity Strategy Unveiled by Biden-Harris Administration
US Senators have introduced a bipartisan bill aimed at blocking the use of foreign technology that poses a national security threat. The bill seeks to establish a formal process for assessing the security risks associated with technology products and services sourced from foreign countries. This would involve the creation of a task force that would evaluate products and services, and make recommendations on their use. The bill would also require federal agencies to develop procurement guidelines that prioritize secure technology products and services, and would encourage the adoption of secure technology standards across the federal government.
The US government has long been concerned about the potential national security risks associated with the use of foreign technology products and services, particularly from China. This new bill seeks to address these concerns by establishing a formal process for assessing the security risks associated with technology sourced from foreign countries. By creating a task force to evaluate products and services, and prioritizing the procurement of secure technology, the bill aims to reduce the risk of sensitive government data being compromised or stolen. This is particularly important given the increasing sophistication of cyberattacks and the growing importance of technology in government operations. The bill is a bipartisan effort to address a critical national security issue, and is likely to receive support from both sides of the aisle.
The US Senate has introduced a bill aimed at blocking the use of foreign technology that poses a national security threat. The bill seeks to establish a formal process for assessing the security risks associated with technology products and services sourced from foreign countries. This would involve the creation of a task force that would evaluate products and services, and make recommendations on their use. The bill would also require federal agencies to develop procurement guidelines that prioritize secure technology products and services, and would encourage the adoption of secure technology standards across the federal government. [read more]
🎙 Podcast Recommendations
Can You Build a Security Program on Open Source?
What would it take to build your entire security program on open source software, tools, and intelligence? Hosted by David Spark, the producer of CISO Series, and Geoff Belknap, CISO, LinkedIn including guests DJ Schleen, distinguished security architect, Yahoo Paranoids. [listen here]
😊 Picture of the week

We hope you enjoyed your weekly digest! ☕🥮
If you liked our content, be a part of our Cybersecurity journey, then you can join our communities below or go to The Cybersecurity Club for resources.
Signing off! Stay safe and we’ll see you soon.
